- Ledger, renowned crypto wallet maker, ignites a public relations fiasco, admitting potential access to users’ keys.
- An unexpected confession on Twitter from Ledger’s support team raises alarms over users’ asset security.
- Amid queries about wallet recovery service, Ledger unveils its untapped capability to make users’ assets vulnerable.
In a shocking turn of events that reverberated across the cryptocurrency landscape, Ledger, a leading manufacturer of crypto wallets, conceded that it holds the latent ability to gain access to user keys. This alarming revelation, which surfaced during a discussion about the company’s new wallet recovery service, has stirred a whirlwind of anxiety and uncertainty among its user base.
Twitter crypto enthusiast foobar @0xfoobar was able to screenshot the tweet of Ledger before it was deleted:
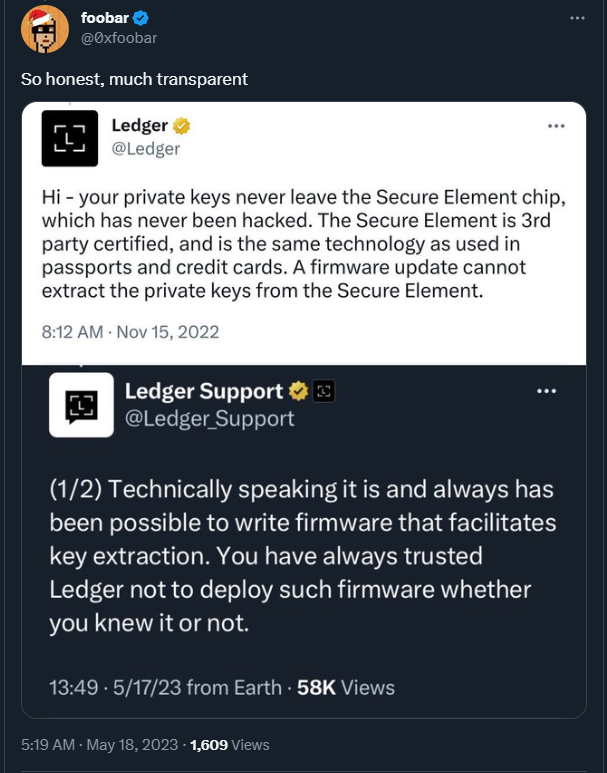
Source: Twitter foobar
Drawing back the curtain on the intricacies of crypto security, Ledger’s support team shared a series of peculiar tweets. These posts suggested that the firm could, if it so chose, compromise its clients’ assets. However, the company added that it has, up until now, refrained from exercising such power. This confession has, undoubtedly, cast a shadow of doubt on the firm’s commitment to ensuring absolute asset security.
The firm’s unexpected admission strikes at the heart of trust, a cornerstone in the relationship between users and their digital wallet providers. As this news ricochets through the crypto community, users are left grappling with their fears, teetering on the edge of uncertainty about the safety of their assets entrusted to Ledger. This unsettling revelation has transformed Ledger from a trusted guardian of assets into a potential vulnerability.
As users come to grips with the sobering truth, the paramount question remains: Is Ledger still a safe haven for their hard-earned cryptocurrency? The crypto community is now in a state of high alert, diligently watching Ledger’s every move. In this climate of uncertainty, it’s clear that Ledger will need to go the extra mile to regain user trust and demonstrate an unequivocal commitment to safeguarding their assets.



